
CrowdStrike, a leader in digital security, recently triggered a global IT meltdown with a software update. This marks one of the few instances in history where a single piece of code has caused such widespread chaos. Notably, past disruptions of this magnitude include the Slammer worm in 2003 and the WannaCry ransomware, which were both deliberate attacks.
The Perfect Storm
On Thursday night, a problem began with an outage in Microsoft’s Azure platform. By Friday, the situation escalated when CrowdStrike released an update that caused Windows computers worldwide to enter a continuous reboot cycle. This perfect storm affected everything from airports and banks to healthcare systems and television stations.
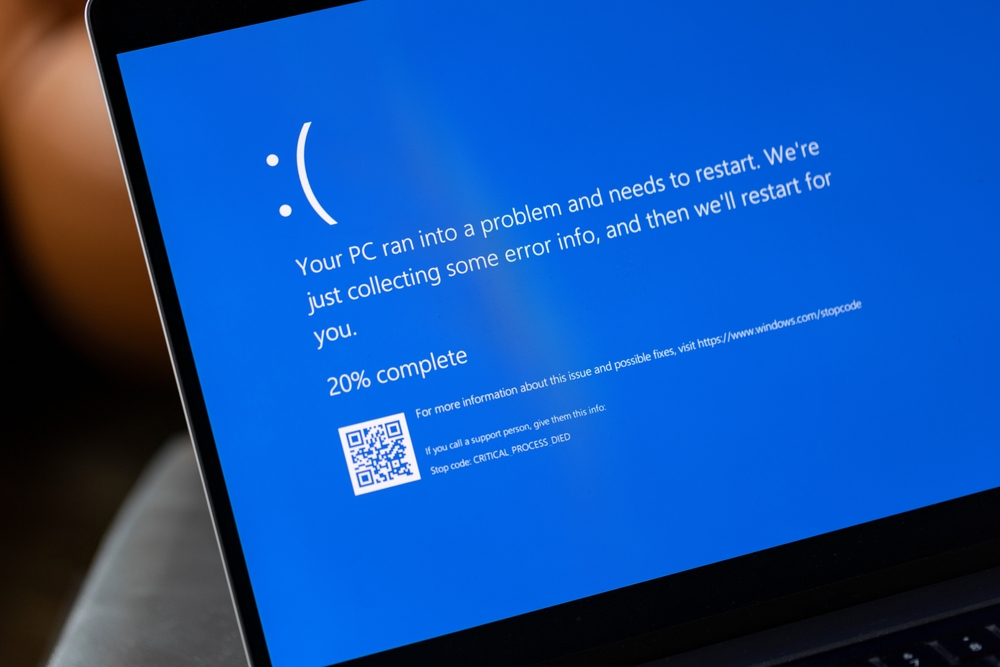
The issue stemmed from a bug in CrowdStrike’s Falcon monitoring system, a powerful antivirus tool that updates itself to combat emerging threats. Unfortunately, this feature backfired, demonstrating that even systems designed to enhance security can compromise it.
Response from CrowdStrike
CrowdStrike CEO George Kurtz quickly responded, attributing the disruption to a “defect” in the Windows update, though Mac and Linux systems remained unaffected. Kurtz emphasized that the malfunction was not caused by a cyberattack and confirmed that a fix was in place. He also issued an apology, noting that returning to normal operations could take some time.

Further investigation revealed the root of the problem was a configuration file in Falcon. This file, intended to improve malware detection, inadvertently triggered an operating system crash. CrowdStrike clarified that the problematic file was not a kernel driver, though it impacted the driver’s functionality.
Despite the severity of the incident, cybersecurity authorities worldwide have ruled out malicious intent. However, the disruption has been profound, affecting global air travel, emergency services, and media broadcasts. In all of these sectors efforts to restore bricked systems are still ongoing. The total cost of the disruptions is yet to be measured but it estimated to be in the billions.

Lessons Learned
The incident highlights the vulnerabilities of our interconnected digital infrastructure and raises questions about the sustainability of automatic updates without manual oversight. Moving forward, this event may prompt a reevaluation of current cybersecurity practices, as CrowdStrike’s experience illustrates the potential risks of such strategies.
For more in Cybersecurity: TunnelVision: Routing Mechanisms Allows Hijacking of VPN Traffic

